Hai semua, saya ingin kongsikan beberapa intipati penting yang dapat saya simpulkan dari kelas seminar yang telah saya sertai. Menerbitkan jurnal dalam pangkalan data terindeks seperti Scopus atau Web of Science secara percuma memerlukan strategi yang teliti. Berikut adalah beberapa tips yang boleh membantu:
- Pilih Jurnal yang Relevan dan Terindeks Scopus/WoS. Semak jurnal yang tidak mengenakan yuran penerbitan. Terdapat juga jurnal yang ditaja oleh universiti atau organisasi yang tidak memerlukan bayaran penerbitan.
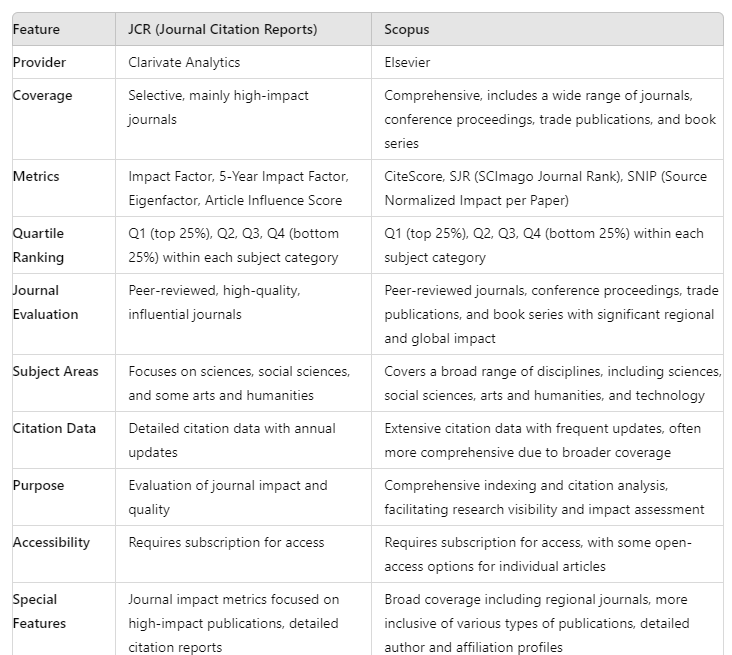
- Gunakan pangkalan data rasmi seperti laman web Scopus atau WoS untuk mencari jurnal yang benar-benar relevan dengan bidang kajian yang dipilih. Pastikan bahawa jurnal masih pada talian di senarai terindeks dan bukan ‘predatory journal’.
- Kenali Skop dan Panduan Jurnal Pengarang. Ikuti panduan penulis dengan teliti untuk memastikan bahawa format dan struktur manuskrip anda sesuai. Lakukan kajian kecil dan buang masa apabila kajian anda tidak sesuai dengan panduan mereka. Anda boleh pilih manuskrip yang lebih kurang kajian – yang telah diterbit oleh jurnal tersebut dan kemudian anda cuba ikut strukturnya.
- Pastikan kajian anda sesuai dengan skop jurnal setiap jurnal mempunyai bidang kajian yang diterima. Ini meningkatkan peluang anda diterima.
- Penulisan Manuskrip Berkualiti Tinggi. Pastikan kajian adalah asli dan memberi pengetahuan baru kepada bidang kajian, memudahkan penerimaan manuskrip. Manuskrip yang jelas dan tidak mempunyai kesalahan tatabahasa dan teknikal lebih mudah diterima. Lakukan sebanyak yang boleh penyuntingan dan semakan dalaman sebelum penghantaran. Gunakan tatabahasa dan perisian seperti Grammarly. Boleh juga hantar kepada proofreader seperti Proofreader by UK, Math Proofreader dan Proofreader Malaysia.
- Proses semakan memerlukan masa. Sebaiknya, rancang dengan baik apabila menghantar manuskrip kerana semakan boleh mengambil masa beberapa bulan. Pastikan tarikh penghantaran anda sesuai dengan jadual tersebut.
- Hindari menghantar ke banyak jurnal serentak. Kebanyakan jurnal tidak membenarkan penghantaran ke jurnal lain secara serentak, jadi penting untuk menghormati peraturan ini. Ia adalah melanggar etika jika anda bertindak menghantar serentak jurnal.
- Berhati-hatilah dengan jurnal predatory yang meminta bayaran penerbitan tanpa menjalankan proses semakan yang teliti. Sentiasa semak kesahihan jurnal dengan memastikan mereka tersenarai dalam pangkalan data rasmi. Anda boleh rujuk penulisan saya yang terdahulu: https://nuuralifahroslan.com/2021/06/24/predatory-journals/)
- Walaupun kebanyakan jurnal akses terbuka mengenakan bayaran penerbitan, terdapat juga yang menawarkan penerbitan secara percuma. Anda boleh mencari jurnal-jurnal ini melalui laman web seperti Directory of Open Access Journals (DOAJ)
Bagaimana cara untuk mengenalpasti jurnal percuma ?
Cara kenal pasti journal tersebut tawarankan Open Access (OA) atau Percuma, juga boleh dilakukan dengan access kepada pangkalan data seperti Scopus, Web of Science dan Elsevier Journal Finder. Kemudian pilih bidang yang anda inginkan. Kebanyakan journal OA ada dinyatakan Open Access atau icon lock. Jika tidak dinyatakan, maka journal tersebut ada menawarkan penerbitan secara percuma.
Semoga membantu!
* Semasa bengkel ini, pengajar menunjukkan kaedah pencarian jurnal percuma dalam database jurnal yang dinyatakan diatas. Bengkel yang sangat berbaloi untuk pelaburan ilmu.